How to Enhance DevOps Security: Your Complete Checklist
Get your complete checklist for DevOps security with our guide. Discover robust DevOps solutions and benefit from our expert DevOps consulting services.
DevOps has emerged as a critical approach to streamline software development and deployment processes in today’s rapidly evolving digital landscape. Organizations can achieve faster release cycles, improved collaboration, and enhanced software quality by integrating development and operations teams. However, with the increasing complexity and interconnectedness of systems, ensuring the security of DevOps environments has become a critical concern. This article will provide a comprehensive checklist to ensure DevOps security, covering various process aspects.
Organizations nowadays have started to understand the potential of DevOps. A survey conducted by Google says that 77% of organizations are still either depending on DevOps or plan to do so shortly. The essential factor behind their decision is the faster deployment of software.
The wide use of DevOps has given rise to security concerns about guarding valuable data against phishing. A new branch of DevOps Security, DevSecOps, has emerged to curb this menace. Companies use DevSecOps to embed security through technology, policies, processes, and strategies.
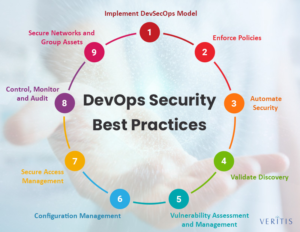
Most convenient DevOps security checklists one must perform to ensure security compliance
Here’s a DevSecOps security checklist to help the DevOps solutions team get on the same page.
Discuss pain points and bottlenecks
Security can be quite a bottleneck to releasing software quickly, but it’s so crucial to minimize or ignore it. An essential step is to generate everyone together — development, security, and operations teams — for a frank discussion regarding the pain points and bottlenecks linked to security. Once everything is up for grabs, create an idea to solve each concern and execute that plan.
Explain the goal
Undoubtedly, the prime objective of DevOps compliance is to try the code from a protection aspect, but taking action without compromising the speed of deployment is difficult! Incorporating DevOps security right from the start implies that security is involved with every process and reduces friction between teams due to misalignment. It may subsequently lead to speeding up release cycles.
Align everyone around a common goal
With a wide variety of assumptions about security and ownership, offering clear goals to the team can provide something tangible to work towards. Moving security forward in the application lifecycle will only help if your team understands its responsibilities and expectations. As an example, aligning on the target of testing more code could translate into faster releases once things are going smoothly. Similarly, establishing a target of improving planning by bringing in a protection champion right from the start means security is associated with every step of the procedure, reducing friction and ultimately speeding up release cycles. A successful DevOps consulting provider practice improves accountability even among non-security team members by creating a culture where reducing security risks is everyone’s responsibility.
Work in smaller chunks
Always make incremental code changes once you shift from DevOps to DevSecOps for security compliance. A tiny bit of code is now easier to examine and deploy than attempting to deploy the whole chunk of code. Trying to deploy a monolithic project won’t only create friction between your DevOps and security teams but can also make you susceptible to making security errors.
Environments in the cloud and DevOps
Teams working on DevOps solutions frequently rely on underdeveloped open-source technologies to manage hundreds of server instances in DevOps cloud environments.
A virtual server like tel-aviv server also offers better DDoS protection which can disrupt traffic on your website.
Due to the enormous scale at which DevOps operates, a simple setup error—such as sharing APIs or SSH keys, for example—could compromise security and harm operations.
Containers and third-party tools
The DevOps environment employs containers and third-party tools like Docker, Kubernetes, CoreOs, etc., to enhance productivity. These ultra-lightweight, portable containers can operate on almost any computer or cloud. However, with the proper controls, these productivity tools can pose security risks because of the sufficient visibility into them. As a result of this, containers need to be adequately scanned, which further elevates the problem.
Tools combine into a single DevOps platform
When teams require the best equipment, security is challenging for everyone. An end-to-end platform that enables DevOps solution teams to depart from waterfall-style processes, streamlines communication, incorporates automation and continuous integration, and offers a single source of truth for security scan results and the status of critical vulnerabilities has proven to be the most effective way to move security left.
Cultural resistance to security
There’s a prevalent belief that implementing security will stifle or halt development. However, detecting a protection defect early in the style and development process costs much less time and effort than being forced to patch the problematic code later in the development cycle.
Automate the code review process
Irrespective of your hard work, you can’t keep your security team aligned with the DevOps team. The truth is that the DevOps solutions team pushes and modifies codes over time. This rate can outpace the security team in the code review process. Without good automation, the output generated will either be super slow or suffer from too little security hygiene.
Checking off items: A checklist for DevOps security
Your company will have a strong security foundation if you follow most of the security recommendations on this checklist. DevOps security, however, is a continuous effort. It would be best to continually incorporate security protocols into every stage of your DevOps life cycle. You must also invest in new technology that streamlines your security process, such as observability, and retrain your staff. DevOps security is worth the investment because this approach makes your applications safer and more compliant while delivering them to market faster!
Wrapping Up!
DevOps practices have revolutionized software development and deployment, enabling organizations to deliver high-quality applications faster. However, ensuring the security of DevOps environments is crucial to protect sensitive data and prevent potential breaches. Organizations can establish robust security measures throughout the DevOps lifecycle by following the comprehensive checklist provided in this article. Whether through secure infrastructure configuration, code management, continuous integration, or incident response, a holistic approach to DevOps security will help safeguard systems and maintain the integrity of software delivery.
Remember, DevOps security is an ongoing effort that requires continuous monitoring, adaptation, and collaboration. Organizations can benefit from expert guidance and specialized tools to enhance their security posture in the ever-evolving threat landscape by partnering with trusted DevOps consulting services or leveraging DevOps solutions providers.